Sha1 Block Diagram
Generally for any hash function h with input x computation of h x is a fast operation.
Sha1 block diagram. The byte hash will come from unit test. Module as shown in the block diagram. Basic hash function diagram 7. The resulting mac algorithm is termed hmac x where x is the hash function used e g.
Message is padded with a 1 and as many 0 s as necessary to bring the message length to 64 bits fewer than an even multiple of 512. The md5 and sha1 are the hashing algorithms where md5 is better than sha in terms of speed. The concept behind these hashing algorithms is that these are used to generate a unique digital fingerprint of data or message which is known as a hash or digest. The sha 1 encryption ip core is a fully compliant implementation of the message digest algorithm sha 256.
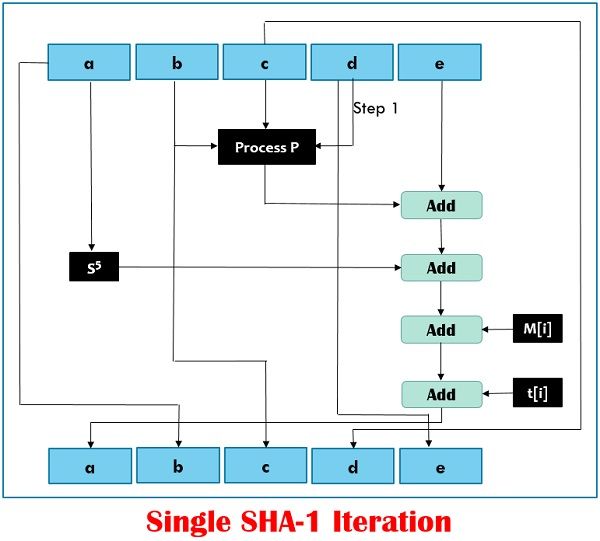
The sha1 engine module applies the sha1 loops on a single 512 bit message block while the input interface module performs the message padding. Hmac sha256 or hmac sha3 the cryptographic strength of the hmac depends upon the cryptographic strength of the underlying hash function the size of its hash output and the size and quality of the key. Sha 1 is a cryptographic function that takes as input a 2 64 bits maximum length message and outputs a 160 bits hash 40 caracters. Sha 1 160 bit message algorithm framework step 1.
However sha1 is more secure as compared to md5. Any cryptographic hash function such as sha 2 or sha 3 may be used in the calculation of an hmac. It was designed by the united states national security agency and is a u s. Popular hash functions generate values between 160 and 512 bits.
It computes a 256 bit message digest for messages of up to 2 64 1 bits developed for easy reuse the sha 1 is available optimized for several technologies with competitive utilization and performance characteristics. Computationally hash functions are much faster than a symmetric encryption. The processing of one 512 bit block is performed in 82 clock cycles and the bit rate achieved is 6 24mbps mhz on the input of the sha1core. In cryptography sha 1 secure hash algorithm 1 is a cryptographic hash function which takes an input and produces a 160 bit 20 byte hash value known as a message digest typically rendered as a hexadecimal number 40 digits long.
Sha 1 is an improvement of sha 0 it was created by the nsa and improve cryptographic security by increasing the number of operations before a collision theory says 2 63 operations however sha 1 is not considered as secure because 2 63 could be. Federal information processing standard.